Cloud environments are becoming too large and complex for organizations, so it has become almost impossible to rely on manual processes. A robust CSPM tool is driven by automation. It automatically and continuously checks for misconfiguration and helps protect organizations from data breaches and leaks. Let us now look at some of the best features offered by CSPM in general, which are also depicted in Figure 2.3:
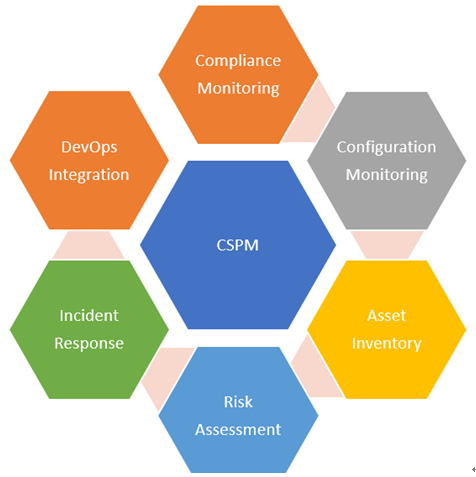
Figure 2.3 – CSPM features
Here are some of the core capabilities of a typical CSPM tool:
- DevSecOps integration: CSPM tools interact with existing DevOps tools sets along with SIEM and SOAR toolsets, allowing for quicker remediation and reaction inside the DevOps toolsets
- Asset discovery and management: CSPM tools allow organizations to discover and inventory their cloud assets, including compute resources, storage, databases, and networking components
- Configuration management: CSPM tools help organizations manage the configuration of their cloud assets, ensuring they comply with security best practices and company policies
- Threat detection and response: CSPM tools use machine learning, behavior analysis, and other advanced techniques to detect security threats in real time and provide automated remediation recommendations
- Compliance management: CSPM tools help organizations ensure their cloud infrastructure complies with industry regulations and standards such as PCI DSS, HIPAA, and SOC 2
- Access control: CSPM tools allow organizations to manage and control access to their cloud assets, including user authentication, authorization, and role-based access control
- Activity monitoring: CSPM tools provide visibility into user activity and resource usage, including API calls, network traffic, and resource utilization
- Reporting and analytics: CSPM tools generate reports and analytics that provide insights into the security posture of an organization’s cloud infrastructure, including trends, anomalies, and areas of improvement
These are some of the key capabilities of CSPM tools, but the specific features and capabilities may vary depending on the tool. Now that you understand the core capabilities of CSPM tools, let us understand the workings of CSPM tools.
